When we
create function app and put it on Azure cloud, they need to be secure. When it
comes to security of Function Apps, there are few options like Azure AD,
Function Level, put them in VNET, secure them through API Manager etc. In this
blog we will see how we can secure our function using Azure AD OAuth 2.0.
We will be
creating Azure App registration and Function App separately then will enable
our function app to use Azure AD as an Identity provider.
Azure AD App Registration:
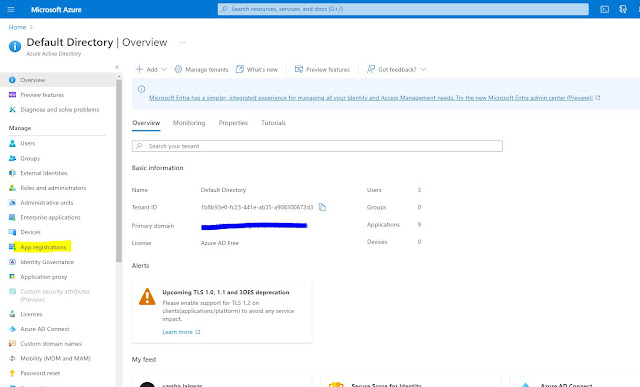
Open azure
portal and click on Azure Active Directory, you should be able to see below
screen.
Click on
New Registration button as highlighted.
Register an
app by providing a Name and supported account type. In my case I have given oauth-demo-fun-app
name and chosen “Single Tenant”
Click on
register to create app registration. An Application (Client) id will be
generated.
Copy the
Application ID and Click on “Expose as API” to add a scope. Use
“api://<Application Id>” that you copied. Click on save and continue.
Give scope name as “user_impersonation”, choose “Admin and users”, provide description and display name as per below screenshot.
Click on
Add Scope
Now let create a new client secret for the API. This credential will be used to call token API. Secret will be appeared only once so make sure you copy it once created otherwise create a new one.
Click on “New Client Secret” and provide description and choose expiry duration.
Note* - From portal you can choose up to 24 months only, if you want to create for longer period or never expired, use PowerShell or terraform code etc.
To verify
if your Token API is working and generating the token properly, click on
Overview and click on the endpoint as per below screenshot
Copy the OAuth 2.0 token endpoint to test it in postman. As per below
Postman
Request:
Method POST
URL: Token
API 2.0 (copy it from endpoint)
Body:
x-www-form-urlencoded
Grant_type: client_credentails
Client_secret: (use the secret that
we created in above step)
Client_id: Application (Client) ID
of the app registration
Scope: api://<application id>
Hit the URL
you should be getting a valid JWT token
Create a
Function App:
This is the
2nd phase where are going to create a function app in the portal.
I’ll be using dotnet runtime, windows based with consumption-based plan.
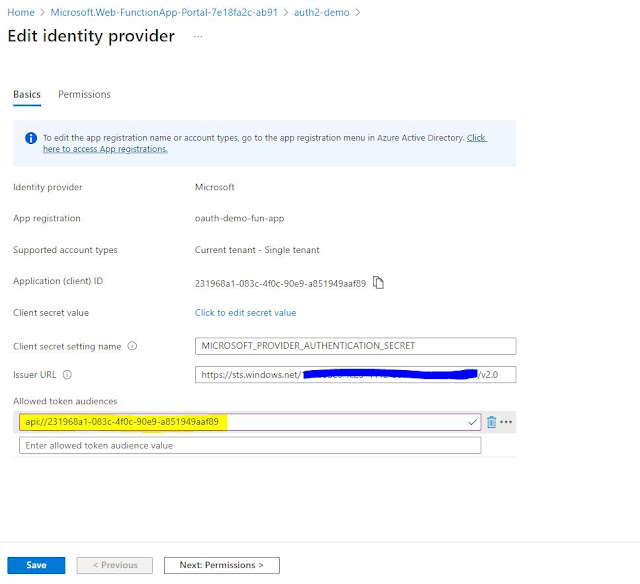
Now there
are two options when it comes to selecting Microsoft as an Identity provider.
You can create one from here or choose an existing one. Since we have created
App registration at the beginning of the blog so we will use that option (which
is existing one).
Click on Add button.
You should be able to see below screen
Value will
be: api://<Application (Client) Id>
You can
again copy this value from App registration overview page.
Create a Function app using C# code from Visual Studio
This is the last phase of our blog where are
will be creating C# function app with “Anonymous” access. This will a
http trigger-based function app like below screen shot
Note* - Anonymous
Access is required if you want to use Azure AD as an ID Provider.
This is going to be very simple function app which is generated by default.
Let’s
publish this function App in our subscription where we created
consumption-based function app.
Once the function app is published let’s try to call it from the postman. Below request is failed as we know it needs a “Authorization” token. It gives me 401 unauthorized access.
Let’s get
the token from the token API. Use the previous token API to get the token. Copy
the token once generated.
OAuth 2.0
is widely used and accepted protocol. You can restrict function App with some other security pattern as per your requirement.
























No comments:
Post a Comment